Encryption is an undeniably significant arrangement of innovations that empowers clients to defend private information in PCs, crosswise over open or private systems, or in other machine-coherent structures.
There is significantly more information in danger of being undermined than any time in recent memory. This, related to the expanding cost of an information rupture, estimated in both “hard” dollar terms like lawful settlements, and “delicate” costs, for example, loss of client steadfastness, utilizes encryption and other information insurance advancements progressively fundamental for associations everything being equal.
For the little and medium-sized market, the perfect information Authentico encryption approach would be both reasonable and effectively coordinated into a complete information reinforcement and business frameworks congruity arrangement. It would incorporate ground-breaking, benchmarks based encryption, and offer a strong key administration work.
Luckily, encryption usefulness can be effectively coordinated into an association’s reinforcement forms, ensuring all information on the organization’s servers and reinforcement gadgets, and all information taken off site for chronicling.
Keys and key administration

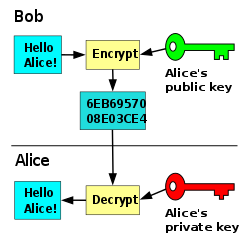
A key is a snippet of data, or parameter, that controls the activity of a cryptography calculation. Present day encryption calculations normally utilize either symmetric or lopsided keys. Deviated key encryption utilizes a couple of keys, called an open key and a private key, and is most appropriate for ensuring information that has a wide group of spectators -, for example, sites with secure access built up for some clients.
Symmetric key techniques utilize a similar key for both encryption and decoding. Symmetric keys are fantastic for use with gadgets and apparatuses in which the need to share keys is exceptionally restricted. This is ordinarily the situation with information reinforcement gadgets, for which one explicitly does not have to permit numerous gatherings access to the key.
If you lose your home key, a locksmith can pick the lock precisely and help you recapture get to. In the event that you lock your keys in the vehicle, there are many specific devices that can enable you to open the entryway. In any case, any encryption technique that permitted this sort of “elective access” in case of a lost key would be lethally unreliable. Nowadays, most scrambled information is basically incomprehensible to hoodlums and totally lost to the proprietor without the fundamental key for unscrambling. This puts huge weight on the proprietor to not overlook the key. It’s imperative to pick a “solid” key, frequently many, numerous characters long, which makes it harder to figure, yet in addition harder to recall. What’s more, recording the key brings its very own undeniable security dangers.
Arranging a fruitful execution
There are six keys to actualizing an encryption ability inside your general information insurance and debacle recuperation system. These speak to the genuine “basic achievement factors.” Get these six right and you’ll have an extremely high likelihood of accomplishment.
- Keep up widespread information recuperation. Any place the encoded information dwells (nearby reinforcement gadget, remote server farm, disconnected media, or file media), you should almost certainly dependably switch the procedure and produce decoded information.
- Select a solitary methodology for all your touchy information. Make certain to pick a methodology that enables you to execute encryption once, and ensure all your delicate information through a solitary, incorporated ability.
- Limit asset sway. Encryption can include some significant pitfalls. Make certain yours is acceptably little. Make certain the CPU load from the encryption procedure is adequately “lightweight” to evade a material rot in the rate at which your frameworks procedure their ordinary work. Spare system transfer speed by compacting information before transmission, and by sending just changed squares of information. Pick a straightforward, amazing, and natural UI.
- Counteract unapproved access to information. Information ought to be encoded so that a “reasonable content” duplicate might be replicated simply after legitimate verification has been given.
- Have a key administration technique. You ought to pick an answer with amazing key administration abilities, making it simple to change keys habitually, recuperate old documents for which the first keys may have been lost, and generally strike a harmony among wellbeing and availability.
- Test ahead of time. You should demonstrate that your answer can both encode (and store scrambled information in all areas) and effectively make clear content from any encoded sources.
Truly, the expense and trouble related with actualizing encryption to increase an association’s information security was essentially excessively overwhelming, particularly for little to medium-sized endeavors. Be that as it may, presently arrangements exist that bring venture class encryption innovation to organizations everything being equal.